Sandbox
Sobre a tecnologia de sandbox
Sandbox é um sistema de detecção de malware que executa um objeto suspeito em uma máquina virtual (VM) com sistema operacional completo e detecta atividades maliciosas do objeto analisando seu comportamento. Se o objeto executa ações maliciosas em uma VM, a sandbox o detecta como malware. As VMs são isoladas da infraestrutura corporativa real.
As sandboxes analisam o comportamento de um objeto durante sua execução, o que as torna eficazes contra malwares que fogem da análise estática. Ao mesmo tempo, em comparação com outros componentes de análise de comportamento, uma sandbox é mais segura, pois não corre o risco de executar um objeto suspeito na infraestrutura real da empresa.
Kaspersky Sandbox
Desenvolvemos nossa própria sandbox há alguns anos. Em nossa infraestrutura, ela é uma das ferramentas de análise de malware, pesquisa e criação de bases de dados antivirais. A sandbox também faz parte da Kaspersky Anti-Targeted Attack Platform e da Kaspersky Threat Intelligence Platform. Ela ajuda a classificar arquivos e URLs como maliciosos ou benignos e fornece informações sobre suas atividades que são úteis para criar regras e algoritmos de detecção.
Características da sandbox
- A sandbox tem como base a virtualização de hardware, o que a torna rápida e estável.
- As VMs estão disponíveis para:
- Sistema operacional Windows (todas as versões de computador pessoal desde o Windows XP, todas as versões de servidor desde o Windows Server 2003)
- Sistema operacional Android (x86, arquitetura de processador ARM)
- A sandbox monitora a interação do processo explorado com o sistema operacional. Em casos suspeitos, a sandbox vai ainda mais longe.
- A sandbox fornece detecção de exploits desde as fases iniciais da exploração. Ela detecta comportamentos típicos de exploits, como o uso de cadeia ROP, pulverização de heap, dinamização de pilha, alteração de tokens de segurança, mudanças suspeitas na proteção da memória e outros. A sandbox é capaz de detectar até os mais avançados exploits usados em ataques direcionados.
Tipos de objetos que podem ser executados
- Windows: qualquer arquivo, por exemplo: *.exe, *.dll, objetos .NET, arquivos do MS Office, PDFs.
- Android: APK (DEX).
- URLs: a sandbox acessa um URL e detecta os seguintes eventos: downloads, JavaScript, execução do Adobe Flash e outros.
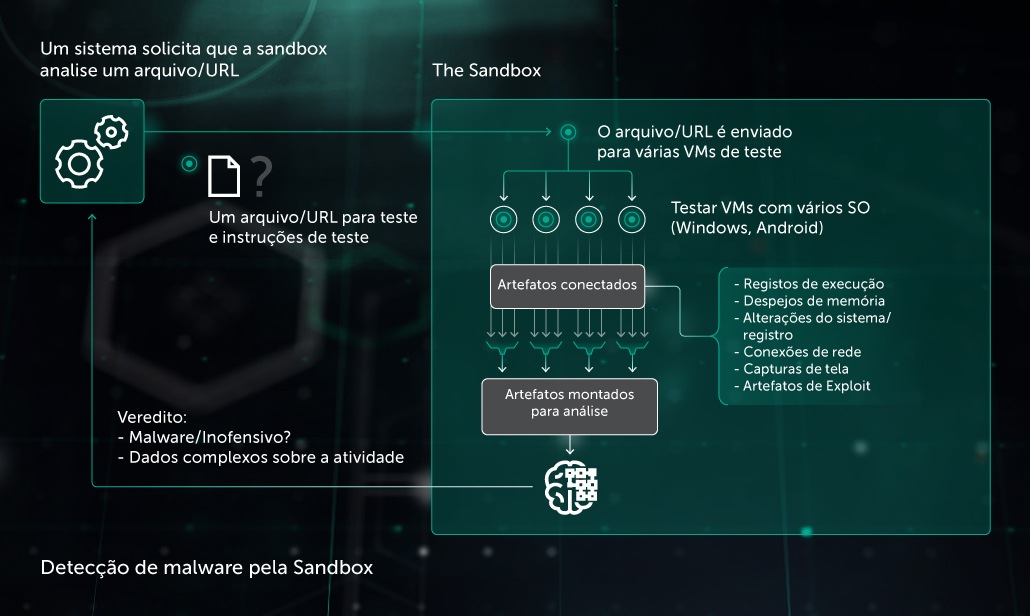
Fluxo de trabalho de detecção de malware
- A sandbox recebe uma solicitação para verificar um objeto (um arquivo ou um URL) de outro componente da solução de segurança com determinadas instruções: sistema operacional e configuração para executar o objeto, parâmetros de execução do objeto, outros aplicativos de terceiros instalados na VM, limite de tempo de teste, etc.
- O objeto testado é executado.
- A sandbox coleta artefatos durante o tempo especificado. Se o objeto interagir com outros processos ou URLs com reputações conhecidas, a sandbox capturará isso.
- A sandbox analisa os artefatos e entrega seu veredito ao sistema solicitante: malware ou benigno. A sandbox adiciona os dados do objeto ao veredito (ID, recursos, logs, detalhes de comportamento), o que pode ajudar em análises posteriores sem a necessidade de uma nova solicitação para a sandbox.
Artefatos coletados pela sandbox
- Logs de execução de aplicativos (chamadas de função de API com seus parâmetros, eventos de execução)
- Despejos de memória
- Despejos de módulos carregados
- Mudanças no sistema de arquivos e no Registro
- Tráfego de rede (arquivos PCAP)
- Capturas de tela (para auditoria e análise manual mais fáceis, se necessário)
- Artefatos da atividade do exploit
Prevenção de evasão
É comum que os malwares atuais tentem detectar e escapar de uma sandbox. Quando sabem que estão sendo executados em uma sandbox, eles podem pular a execução de alguma atividade maliciosa, apagar-se dos discos, encerrar-se ou usar alguma outra técnica de evasão.
Um recurso mais simples de monitoramento de sandbox de hardware (por exemplo, funções de API de interceptação) deixaria rastros indicando que um processo suspeito está sendo observado. Por isso, implementamos outras técnicas de monitoramento que não são intrusivas e não deixam rastros visíveis para o objeto verificado. A sandbox controla a CPU e a RAM, mas não modifica a operação do processo, a memória, bibliotecas do sistema no disco e na memória, o que não deixa rastros de monitoramento.
Também monitoramos novas técnicas de evasão emergentes e ajustamos nossa sandbox para neutralizá-las, por exemplo:
Evasão A: o ambiente da sandbox é típico de algumas sandboxes de marcas conhecidas. O malware o reconhece e evita a detecção.
Combate à evasão A: nossa sandbox define aleatoriamente o ambiente da VM antes do início da VM.
Evasão B: o malware consegue detectar o ambiente da sandbox por meio da falta de atividade do usuário. Para que alguns malware sejam executados, o usuário precisa inserir uma senha em um e-mail, clicar em um assistente ou fazer outras coisas "humanas". Muitas sandboxes não emulam isso e, portanto, não veem o malware detonar.
Combate à evasão B: nossa sandbox emula ações do usuário: movimentos do mouse, rolagem de documentos abertos por ela. Nossa sandbox também faz várias coisas que os usuários fazem para ativar um malware.
Ataques revelados pela Kaspersky Sandbox
Exemplos de novas ondas de ataques direcionados descobertos por sandboxes em produtos de infraestrutura da Kaspersky em 2016-2017: Sofacy (outubro de 2017), Zero.T (outubro, novembro de 2016, abril de 2017), Enfal (setembro, outubro, novembro de 2016), Freakyshelly (outubro de 2016), NetTraveller (agosto de 2016), CobaltGoblin (agosto de 2016), Microcin (junho de 2016) e outros.

